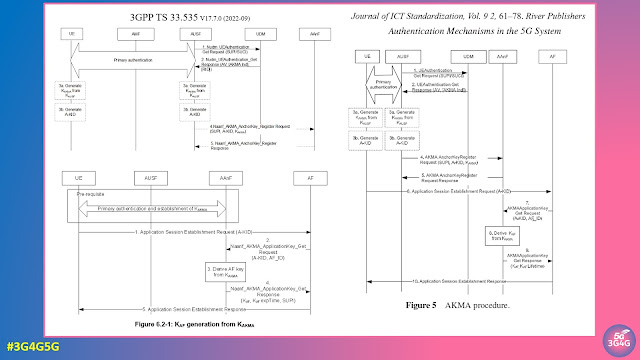
3GPP Release 17 introduced a new feature called AKMA (Authentication and Key Management for Applications), the goal of which is to enable the authentication and generation of application keys based on 3GPP credentials for all UE types in the 5G System, especially IoT devices, ensuring to bootstrap the security between the UE and the applications in the 5G system.
3GPP TR 21.917 has an excellent summary as follows:
Authentication and key management for applications based on 3GPP credential in 5G (AKMA) is a cellular-network-based delegated authentication system specified for the 5G system, helping establish a secure tunnel between the end user and the application server. Using AKMA, a user can log in to an application service only based on the 3GPP credential which is the permanent key stored in the user’s tamper-resistant smart card UICC. The application service provider can also delegate the task of user authentication to the mobile network operator by using AKMA.
The AKMA architecture and procedures are specified by SA3 in TS 33.535, with the related study showing how its general principles are derived documented in TR 33.835. The AKMA feature introduces a new Network Function into the 5G system, which is the AKMA Anchor Function (AAnF). Its detailed services and API definitions are specified by CT3 in TS 29.535. Earlier generations of cellular networks include two similar standards specified by SA3, which are generic bootstrapping architecture (GBA) and battery-efficient security for very low throughput machine type communication devices (BEST). Since the AKMA feature is deemed as a successor of these systems, the work is launched by SA3 without the involvement of stage 1.
In the latest issue of 3GPP Highlights Magazine, Suresh Nair, 3GPP Working Group SA3 Chair, Saurabh Khare & Jing Ping (Nokia) has explained the AKMA procedure. The article is also available on 3GPP website here. The article lists the following as AKMA advantages:
- Since the AKMA framework uses authentication and authorization of the UE leveraging the PLMN credentials stored on the USIM, this becomes as strong as the network primary authentication and subsequent keys derived further to UE and Application Function (AF) interface.
- The Application Functions can leverage the authentication service provided by the AKMA Anchor Function (AAnF) without additional CAPEX and OPEX.
- The architecture provides a direct interface between the UE and the AF where a customized application-specific interface can be built, including the key management, key lifetime extension, etc.
The Journal of ICT Standardization has a paper on Authentication Mechanisms in the 5G System. It details AKMA and much more. It's a great place to start for anyone new looking to understand different 5G Authentication Mechanisms.
Related Posts:
- The 3G4G Blog: 3GPP Release 17 Description and Summary of Work Items
- The 3G4G Blog: Lawful Intelligence and Interception in 5G World with Data and OTT Apps
- The 3G4G Blog: 5G and Cyber Security
- The 3G4G Blog: Realizing Zero Trust Architecture for 5G Networks
- The 3G4G Blog: AT&T Cybersecurity Experts Provide 5G Security Overview
- The 3G4G Blog: Everything you need to know about 5G Security
- The 3G4G Blog: Introduction to 3GPP Security in Mobile Cellular Networks
- The 3G4G Blog: Initiative to Remove Non-inclusive terms from 3GPP Specifications
- The 3G4G Blog: 3GPP 5G Non Terrestrial Networks (NTN) Standardization Update
- The 3G4G Blog: 3GPP Explains TSG CT Work on UAS Connectivity, Identification and Tracking