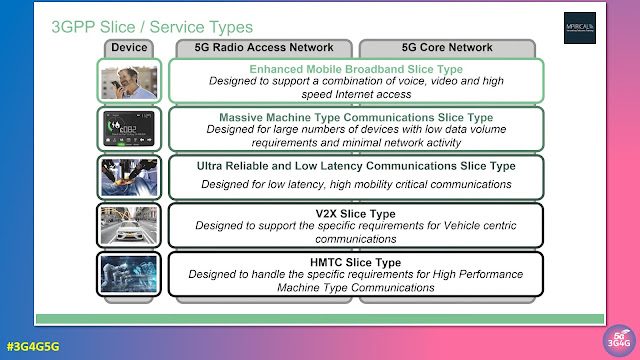
The following list is from the v1.0.0 table of contents to make it easier to find the list of topics. If it interests you, download the latest version technical report from the directory here.
5 Satellite / Non-Terrestrial Network (NTN)
5.1 General aspects
5.1.1 User plane: “5G system with satellite backhaul”
5.1.2 Discontinuous coverage: “Satellite access Phase 2”
5.1.3 Radio: "NR NTN enhancements"
5.1.4 Charging and Management aspects of Satelite
5.2 Specific aspects
5.2.1 IoT (Internet of Things) NTN enhancements
5.2.2 Guidelines for Extra-territorial 5G Systems
5.2.3 5G system with satellite access to Support Control and/or Video Surveillance
5.2.4 Introduction of the satellite L-/S-band for NR
5.2.5 Other band-related aspects of satellite
6 Internet of Things (IoT), Machine-Type Communication (MTC)
6.1 Personal IoT and Residential networks
6.2 Enhanced support of Reduced Capability (RedCap) NR devices
6.3 NR RedCap UE with long eDRX for RRC_INACTIVE State
6.4 Application layer support for Personal IoT Network
6.5 5G Timing Resiliency System
6.6 Mobile Terminated-Small Data Transmission (MT-SDT) for NR
6.7 Adding new NR FDD bands for RedCap in Rel-18
6.8 Signal level Enhanced Network Selection
6.9 IoT NTN enhancements
7 Energy Efficiency (EE)
7.1 Enhancements of EE for 5G Phase 2
7.2 Network energy savings for NR
7.3 Smart Energy and Infrastructure
8 Uncrewed Aerial Vehicles (UAV), UAS, UAM
8.1 Architecture for UAV and UAM Phase 2
8.2 Architecture for UAS Applications, Phase 2
8.3 NR support for UAV
8.4 Enhanced LTE Support for UAV
9 Sidelink, Proximity, Location and Positioning
9.1 5GC LoCation Services - Phase 3
9.2 Expanded and improved NR positioning
9.3 NR sidelink evolution
9.4 NR sidelink relay enhancements
9.5 Proximity-based Services in 5GS Phase 2
9.6 Ranging-based Service and sidelink positioning
9.7 Mobile Terminated-Small Data Transmission (MT-SDT) for NR
9.8 5G-enabled fused location service capability exposure
10 Verticals, Industries, Factories, Northbound API
10.1 Low Power High Accuracy Positioning for industrial IoT scenarios
10.2 Application enablement aspects for subscriber-aware northbound API access
10.3 Smart Energy and Infrastructure
10.4 Generic group management, exposure and communication enhancements
10.5 Service Enabler Architecture Layer for Verticals Phase 3
10.6 SEAL data delivery enabler for vertical applications
10.7 Rel-18 Enhancements of 3GPP Northbound and Application Layer interfaces and APIs
10.8 Charging Aspects of B2B
10.9 NRF API enhancements to avoid signalling and storing of redundant data
10.10 GBA_U Based APIs
10.11 Other aspects
11 Artificial Intelligence (AI)/Machine Learning (ML)
11.1 AI/ML model transfer in 5GS
11.2 AI/ML for NG-RAN
11.3 AI/ML management & charging
11.4 NEF Charging enhancement to support AI/ML in 5GS
12 Multicast and Broadcast Services (MBS)
12.1 5G MBS Phase 2
12.2 Enhancements of NR MBS
12.3 UE pre-configuration for 5MBS
12.4 Other MBS aspects
13 Network Slicing
13.1 Network Slicing Phase 3
13.2 Enhancement of NSAC for maximum number of UEs with at least one PDU session/PDN connection
13.3 Enhancement of Network Slicing UICC application for network slice-specific authentication and authorization
13.4 Charging Aspects of Network Slicing Phase 2
13.5 Charging Aspects for NSSAA
13.6 Charging enhancement for Network Slice based wholesale in roaming
13.7 Network Slice Capability Exposure for Application Layer Enablement
13.8 Other slice aspects
14 eXtended, Augmented and Virtual Reality (XR, AR, VR), immersive
14.1 XR (eXtended Reality) enhancements for NR
14.2 Media Capabilities for Augmented Reality
14.3 Real-time Transport Protocol Configurations
14.4 Immersive Audio for Split Rendering Scenarios (ISAR)
14.5 Immersive Real-time Communication for WebRTC
14.6 IMS-based AR Conversational Services
14.7 Split Rendering Media Service Enabler
14.8 Extended Reality and Media service (XRM)
14.9 Other XR/AR/VR items
15 Mission Critical and emergencies
15.1 Enhanced Mission Critical Push-to-talk architecture phase 4
15.2 Gateway UE function for Mission Critical Communication
15.3 Mission Critical Services over 5MBS
15.4 Mission Critical Services over 5GProSe
15.5 Mission Critical ad hoc group Communications
15.6 Other Mission Critical aspects
16 Transportations (Railways, V2X, aerial)
16.1 MBS support for V2X services
16.2 Air-to-ground network for NR
16.4 Interconnection and Migration Aspects for Railways
16.5 Application layer support for V2X services; Phase 3
16.6 Enhanced NR support for high speed train scenario in frequency range 2 (FR2)
17 User Plane traffic and services
17.1 Enhanced Multiparty RTT
17.2 5G-Advanced media profiles for messaging services
17.3 Charging Aspects of IMS Data Channel
17.4 Evolution of IMS Multimedia Telephony Service
17.5 Access Traffic Steering, Switch and Splitting support in the 5G system architecture; Phase 3
17.6 UPF enhancement for Exposure and SBA
17.7 Tactile and multi-modality communication services
17.8 UE Testing Phase 2
17.9 5G Media Streaming Protocols Phase 2
17.10 EVS Codec Extension for Immersive Voice and Audio Services
17.11 Other User Plane traffic and services items
18 Edge computing
18.1 Edge Computing Phase 2
18.2 Architecture for enabling Edge Applications Phase 2
18.3 Edge Application Standards in 3GPP and alignment with External Organizations
19 Non-Public Networks
19.1 Non-Public Networks Phase 2
19.2 5G Networks Providing Access to Localized Services
19.3 Non-Public Networks Phase 2
20 AM and UE Policy
20.1 5G AM Policy
20.2 Enhancement of 5G UE Policy
20.3 Dynamically Changing AM Policies in the 5GC Phase 2
20.4 Spending Limits for AM and UE Policies in the 5GC
20.5 Rel-18 Enhancements of UE Policy
21 Service-based items
21.1 Enhancements on Service-based support for SMS in 5GC
21.2 Service based management architecture
21.3 Automated certificate management in SBA
21.4 Security Aspects of the 5G Service Based Architecture Phase 2
21.5 Service Based Interface Protocol Improvements Release 18
22 Security-centric aspects
22.1 IETF DTLS protocol profile for AKMA and GBA
22.2 IETF OSCORE protocol profiles for GBA and AKMA
22.3 Home network triggered primary authentication
22.4 AKMA phase 2
22.5 5G Security Assurance Specification (SCAS) for the Policy Control Function (PCF)
22.6 Security aspects on User Consent for 3GPP services Phase 2
22.7 SCAS for split-gNB product classes
22.8 Security Assurance Specification for AKMA Anchor Function Function (AAnF)
22.9 Other security-centric items
23 NR-only items
23.1 Not band-centric
23.1.1 NR network-controlled repeaters
23.1.2 Enhancement of MIMO OTA requirement for NR UEs
23.1.3 NR MIMO evolution for downlink and uplink
23.1.4 Further NR mobility enhancements
23.1.5 In-Device Co-existence (IDC) enhancements for NR and MR-DC
23.1.6 Even Further RRM enhancement for NR and MR-DC
23.1.7 Dual Transmission Reception (TxRx) Multi-SIM for NR
23.1.8 NR support for dedicated spectrum less than 5MHz for FR1
23.1.9 Enhancement of NR Dynamic Spectrum Sharing (DSS)
23.1.10 Multi-carrier enhancements for NR
23.1.11 NR RF requirements enhancement for frequency range 2 (FR2), Phase 3
23.1.12 Requirement for NR frequency range 2 (FR2) multi-Rx chain DL reception
23.1.13 Support of intra-band non-collocated EN-DC/NR-CA deployment
23.1.14 Further enhancements on NR and MR-DC measurement gaps and measurements without gaps
23.1.15 Further RF requirements enhancement for NR and EN-DC in frequency range 1 (FR1)
23.1.16 Other non-band related items
23.2 Band-centric
23.2.1 Enhancements of NR shared spectrum bands
23.2.2 Addition of FDD NR bands using the uplink from n28 and the downlink of n75 and n76
23.2.3 Complete the specification support for BandWidth Part operation without restriction in NR
23.2.4 Other NR band related topics
24 LTE-only items
24.1 High Power UE (Power Class 2) for LTE FDD Band 14
24.2 Other LTE-only items
25 NR and LTE items
25.1 4Rx handheld UE for low NR bands (<1GHz) and/or 3Tx for NR inter-band UL Carrier Aggregation (CA) and EN-DC
25.2 Enhancement of UE TRP and TRS requirements and test methodologies for FR1 (NR SA and EN-DC)
25.3 Other items
26 Network automation
26.1 Enablers for Network Automation for 5G phase 3
26.2 Enhancement of Network Automation Enablers
27 Other aspects
27.1 Support for Wireless and Wireline Convergence Phase 2
27.2 Secondary DN Authentication and authorization in EPC IWK cases
27.3 Mobile IAB (Integrated Access and Backhaul) for NR
27.4 Further NR coverage enhancements
27.5 NR demodulation performance evolution
27.6 NR channel raster enhancement
27.7 BS/UE EMC enhancements for NR and LTE
27.8 Enhancement on NR QoE management and optimizations for diverse services
27.9 Additional NRM features phase 2
27.10 Further enhancement of data collection for SON (Self-Organising Networks)/MDT (Minimization of Drive Tests) in NR and EN-DC
27.11 Self-Configuration of RAN Network Entities
27.12 Enhancement of Shared Data ID and Handling
27.13 Message Service within the 5G system Phase 2
27.14 Security Assurance Specification (SCAS) Phase 2
27.15 Vehicle-Mounted Relays
27.16 SECAM and SCAS for 3GPP virtualized network products
27.17 SECAM and SCAS for 3GPP virtualized network products
27.18 MPS for Supplementary Services
27.19 Rel-18 enhancements of session management policy control
27.20 Seamless UE context recovery
27.21 Extensions to the TSC Framework to support DetNet
27.22 Multiple location report for MT-LR Immediate Location Request for regulatory services
27.23 Enhancement of Application Detection Event Exposure
27.24 General Support of IPv6 Prefix Delegation in 5GS
27.25 5G Timing Resiliency System
27.26 MPS when access to EPC/5GC is WLAN
27.27 Data Integrity in 5GS
27.28 Security Enhancement on RRCResumeRequest Message Protection
28 Administration, Operation, Maintenance and Charging-centric Features
28.1 Introduction
28.2 Intent driven Management Service for Mobile Network phase 2
28.3 Management of cloud-native Virtualized Network Functions
28.4 Management of Trace/MDT phase 2
28.5 Security Assurance Specification for Management Function (MnF)
28.6 5G performance measurements and KPIs phase 3
28.7 Access control for management service
28.8 Management Aspects related to NWDAF
28.9 Management Aspect of 5GLAN
28.10 Charging Aspects of TSN
28.11 CHF Distributed Availability
28.12 Management Data Analytics phase 2
28.12 5G System Enabler for Service Function Chaining
28.13 Other Management-centric items
29 Other Rel-18 Topics