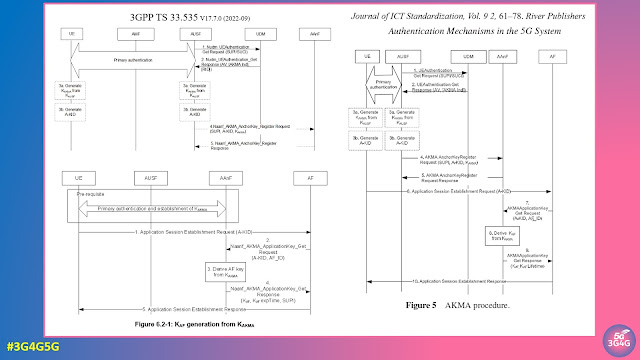
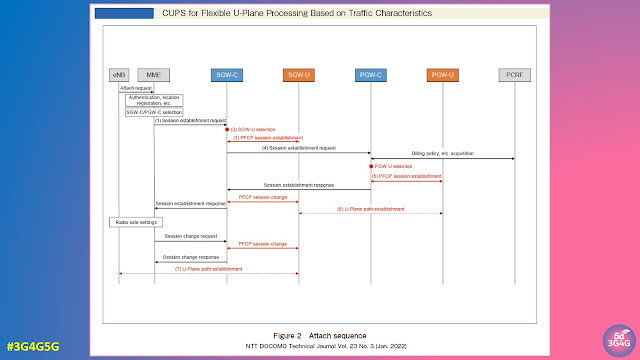
Power-saving methodologies have been integral to all generations of 3GPP technologies, aimed at reducing the power consumption of user equipment (UEs) and other battery-dependent devices. Some of the stringent requirements of 5G, such as achieving a 10-year battery life for certain IoT devices, have necessitated further optimisation of power consumption. To address this, 3GPP Release 16 introduced the Wake-Up Signal (WUS) power-saving mechanism, designed to significantly reduce energy usage in UEs. For a detailed technical explanation, ShareTechnote provides an excellent overview.
The concept of wake-up radios has been explored for over a decade. In a 2017 blog post, Ericsson highlighted how researchers had been working on designing wake-up radios and receivers, initially aimed at IEEE 802.11 (Wi-Fi) technologies. This idea later gained traction in 3GPP discussions, culminating in a study conducted during Release 18. The findings are comprehensively documented in 3GPP TR 38.869: Study on low-power wake-up signal and receiver for NR (Release 18).
Quoting from the introduction of 3GPP 38.869:
5G systems are designed and developed targeting for both mobile telephony and vertical use cases. Besides latency, reliability, and availability, UE energy efficiency is also critical to 5G. Currently, 5G devices may have to be recharged per week or day, depending on individual's usage time. In general, 5G devices consume tens of milliwatts in RRC idle/inactive state and hundreds of milliwatts in RRC connected state. Designs to prolong battery life is a necessity for improving energy efficiency as well as for better user experience.
Energy efficiency is even more critical for UEs without a continuous energy source, e.g., UEs using small rechargeable and single coin cell batteries. Among vertical use cases, sensors and actuators are deployed extensively for monitoring, measuring, charging, etc. Generally, their batteries are not rechargeable and expected to last at least few years as described in TR 38.875. Wearables include smart watches, rings, eHealth related devices, and medical monitoring devices. With typical battery capacity, it is challenging to sustain up to 1-2 weeks as required.
The power consumption depends on the configured length of wake-up periods, e.g., paging cycle. To meet the battery life requirements above, eDRX cycle with large value is expected to be used, resulting in high latency, which is not suitable for such services with requirements of both long battery life and low latency. For example, in fire detection and extinguishment use case, fire shutters shall be closed and fire sprinklers shall be turned on by the actuators within 1 to 2 seconds from the time the fire is detected by sensors, long eDRX cycle cannot meet the delay requirements. eDRX is apparently not suitable for latency-critical use cases. Thus, the intention is to study ultra-low power mechanism that can support low latency in Rel-18, e.g. lower than eDRX latency.
Currently, UEs need to periodically wake up once per DRX cycle, which dominates the power consumption in periods with no signalling or data traffic. If UEs are able to wake up only when they are triggered, e.g., paging, power consumption could be dramatically reduced. This can be achieved by using a wake-up signal to trigger the main radio and a separate receiver which has the ability to monitor wake-up signal with ultra-low power consumption. Main radio works for data transmission and reception, which can be turned off or set to deep sleep unless it is turned on.
The power consumption for monitoring wake-up signal depends on the wake-up signal design and the hardware module of the wake-up receiver used for signal detecting and processing.
The study should primarily target low-power WUS/WUR for power-sensitive, small form-factor devices including IoT use cases (such as industrial sensors, controllers) and wearables. Other use cases are not precluded, e.g.XR/smart glasses, smart phones.
As opposed to the work on UE power savings in previous releases, this study will not require existing signals to be used as WUS. All WUS solutions identified shall be able to operate in a cell supporting legacy UEs. Solutions should target substantial gains compared to the existing Rel-15/16/17 UE power saving mechanisms. Other aspects such as detection performance, coverage, UE complexity, should be covered by the evaluation.
The Bridge Toward 6G: 5G-Advanced Evolution in 3GPP Release 19 by Xingqin Lin, @NVIDIA - https://t.co/O1d8jnB9MY#Free5Gtraining #3G4G5G #3GPP #5G #5GAdvanced #6G #AIML #NGRAN #XR #UAV #LPWUS #LPWUR #HighPerforming #LTM #SBFD #Femtocell #NTN #WAB #Relay pic.twitter.com/aSC9FuruC7
— Free 5G Training (@5Gtraining) January 2, 2024
Qualcomm's blog post looking at 'How will wireless innovations foster a greener, more sustainable future?' is also worth reading on this topic.
Related Posts:
- The 3G4G Blog: 3GPP TSG RAN and TSG SA Release-19 Workshop Summary
- The 3G4G Blog: ETSI's Summit on Sustainability: ICT Standards for a Greener World
- The 3G4G Blog: Four Ways 5G Can Improve the Battery Life of User Equipment (UE)
- The 3G4G Blog: Energy Consumption in Mobile Networks and RAN Power Saving Schemes
- The 3G4G Blog: Reducing 5G Device Power Consumption Using Connected-mode Discontinuous Reception (C-DRX)
- The 3G4G Blog: Mobile Initiated Connection Only (MICO) mode in 5G System