Telecom security rarely stands still. Each year brings new technologies, new attack paths, and new operational realities. Yet 2025 was not defined by dramatic new exploits or spectacular network failures. Instead, it became a year that highlighted how persistent, patient and methodical modern telecom attackers have become.
The recent SecurityGen Year-End Telecom Security Webinar offered a detailed look back at what the industry experienced during 2025. The session pulled together research findings, real world incidents and practical lessons from across multiple domains, including legacy signalling, eSIM ecosystems, VoLTE vulnerabilities and the emerging world of satellite-based mobile connectivity.
For anyone working in mobile networks, the message was clear. The threats are evolving, but many of the core problems remain stubbornly familiar.
A Year of Stealth Rather Than Spectacle
One of the most important themes from the webinar was that 2025 did not bring a wave of highly visible disruptive telecom attacks. Instead, it was characterised by quiet, low profile intrusions that often went undetected for long periods.
Operators around the world reported that attackers increasingly favoured living-off-the-land techniques. Rather than deploying noisy malware, intruders looked for ways to gain legitimate access to core systems and remain hidden. Lawful interception platforms, subscriber databases such as HLR and HSS, and internal management platforms were all targeted.
The primary objective in many cases was intelligence collection. Attackers were interested in call data, subscriber information and network topology rather than immediate disruption. This shift in motivation makes detection far more difficult, as there are often few obvious signs of compromise.
At the same time, automation has become a defining feature on both sides of the security battle. Operators are investing heavily in AI and machine learning to identify abnormal behaviour. Attackers are doing exactly the same, using automation to scale phishing campaigns and to accelerate exploit development.
Despite all this technology, basic security discipline continues to be a major challenge. A significant proportion of incidents still originate from human error, poor operational practices or simple failure to apply patches. The industry continues to invest billions in cybersecurity, but much of that effort is consumed by reporting and compliance activities rather than direct threat mitigation.
eSIM Security Comes into Sharp Focus
The transition from physical SIM cards to eSIM and remote provisioning is one of the most significant structural changes in the mobile industry. It offers clear benefits in terms of flexibility and user experience. However, the webinar highlighted that it also introduces entirely new security concerns.
Traditional SIM security models relied heavily on physical control. Fraudsters needed access to large numbers of real SIM cards to operate at scale. With eSIM, many of those physical constraints disappear. Remote provisioning expands the number of parties involved in the connectivity chain, including resellers and intermediaries who may not always operate under strict regulatory oversight.
During 2025 several major SIM farm operations were dismantled by law enforcement. These infrastructures contained tens of thousands of active SIM cards and were used for large scale fraud, smishing campaigns and automated account creation. While such operations existed long before eSIM, the technology has the potential to make them even easier to deploy and manage.
Research discussed in the session pointed to additional concerns. Analysis of travel eSIM services revealed issues such as cross-border routing of management traffic, excessive levels of control granted to resellers, and lifecycle management weaknesses that could potentially be abused by attackers. In some cases, resellers were found to have capabilities similar to full mobile operators, but without equivalent governance or transparency.
The conclusion was not that eSIM is inherently insecure. The technology itself uses strong encryption and robust mechanisms. The problem lies in the wider ecosystem of trust boundaries, partners and processes that surround it. Securing eSIM therefore requires cooperation between operators, vendors, regulators and service providers.
SS7 Remains a Persistent Weak Point
Few topics in telecom security generate as much ongoing concern as SS7. Despite being a technology from a previous era, it remains deeply embedded in global mobile infrastructure. The webinar dedicated significant attention to why SS7 continues to be exploited in 2025 and why it is likely to remain a problem for many years to come.
Throughout the year, media reports and research papers continued to demonstrate practical abuses of SS7 signalling. Attackers probed networks, attempted to bypass signalling firewalls and looked for new ways to manipulate protocol behaviour. Techniques such as parameter manipulation and protocol parsing tricks were highlighted as methods that can sometimes evade existing protections.
One particularly interesting demonstration showed how SS7 messages could be used as a covert channel for data exfiltration. By embedding information inside otherwise legitimate signalling transactions, attackers can potentially move data across networks without triggering traditional security alarms.
Perhaps the most striking point raised was how little progress has been made in eliminating SS7 dependencies. Analysis of global network deployments showed that only a handful of countries operate mobile networks entirely without SS7. Everywhere else, the protocol remains a foundational element of roaming and interconnect.
As a result, even operators that have invested heavily in 4G and 5G security can still be undermined by weaknesses in this legacy layer. The uncomfortable reality is that SS7 vulnerabilities will continue to be exploited well into 2026 and beyond.
VoLTE and Modern Core Network Risks
While legacy protocols remain a problem, modern technologies are not immune. VoLTE infrastructure in particular was identified as an increasingly attractive target.
VoLTE relies on complex interactions between signalling systems, IP multimedia subsystems and subscriber databases. Weaknesses in configuration or interconnection can open the door to call interception, fraud or denial of service. Several real world incidents during 2025 demonstrated that attackers are actively exploring these paths.
The move toward fully virtualised and cloud-native mobile cores also introduces new operational challenges. Telecom networks now resemble large IT environments, complete with the same risks around misconfiguration, insecure APIs and exposed management interfaces.
The Emerging Security Challenge of 5G Satellites
One of the most forward-looking parts of the webinar focused on non-terrestrial networks and direct-to-device satellite connectivity. What was once a concept for the distant future is rapidly becoming a commercial reality.
Satellite integration promises to extend 5G coverage to remote areas, oceans and disaster zones. However, it also changes the security model in fundamental ways. Satellites can act either as simple relay systems or as active components of the mobile radio access network. In both cases, new threat vectors emerge.
Potential issues discussed included the risk of denial of service against shared satellite resources, difficulties in applying traditional radio security controls in space-based equipment, and the possibility of more precise user tracking due to the way satellite systems handle location information.
Experts from the space cybersecurity community explained how vulnerabilities in mission control software and ground segment infrastructure could be exploited. Much of this software was originally designed for isolated environments and is only now being connected to wider networks and the internet.
As telecom networks expand beyond the boundaries of the Earth, security responsibilities extend with them. Operators will need to think not only about terrestrial threats but also about risks originating from space-based components.
The Human Factor and the Skills Gap
Technology was only part of the story. Another recurring theme was the global shortage of skilled telecom cybersecurity professionals.
Studies referenced in the session suggested that millions of additional specialists are needed worldwide, yet only a fraction of that demand can currently be filled. Many security teams are overwhelmed by the sheer volume of alerts and data they must process.
This shortage has real consequences. When teams are stretched thin, patching is delayed, anomalies are missed and complex investigations become difficult to sustain. The panel emphasised that throwing more tools at the problem is not enough. Organisations must focus on training, automation and smarter operational processes.
Automation and AI-driven analysis were presented as essential enablers. Given the scale of modern mobile networks, it is simply not feasible for human analysts to monitor every signalling protocol, every core interface and every emerging technology manually.
Preparing for 2026
Looking ahead, the experts agreed on several broad trends. Attacks on legacy systems such as SS7 will continue. Fraudsters will increasingly target eSIM provisioning processes. VoLTE and 5G core components will face growing scrutiny. Satellite-based connectivity will introduce new and unfamiliar security questions.
Perhaps most importantly, the line between traditional telecom security and general cybersecurity will continue to blur. Mobile networks are now large, distributed IT platforms, and they inherit all the complexities that come with that transformation.
Operators, regulators and vendors must therefore adopt a holistic view. Investment must go beyond compliance reporting and focus on practical defences, real time monitoring and collaborative intelligence sharing.
Final Reflections
The SecurityGen webinar provided a valuable snapshot of an industry at a crossroads. Telecom networks are becoming more advanced and more capable, but also more complex and interconnected than ever before.
2025 demonstrated that attackers do not always need new vulnerabilities. Often they succeed simply by exploiting old weaknesses in smarter ways. The challenge for 2026 is to close those gaps while also preparing for the technologies that are only just beginning to emerge.
For those involved in telecom security, the full discussion is well worth watching. The complete webinar recording can be viewed below:
Related Posts:
- The 3G4G Blog: Evolving Communication Security Towards 6G at the ETSI Security Conference 2025
- The 3G4G Blog: Detection of Real-world Fake Base Station (FBS) Attacks in Thailand
- The 3G4G Blog: Attack Surfaces for Different Generations of Mobile Technologies
- The 3G4G Blog: Presentations from ETSI Security Conference 2023
- The 3G4G Blog: Top 10 New (2022) Security Standards That You Need to Know About!
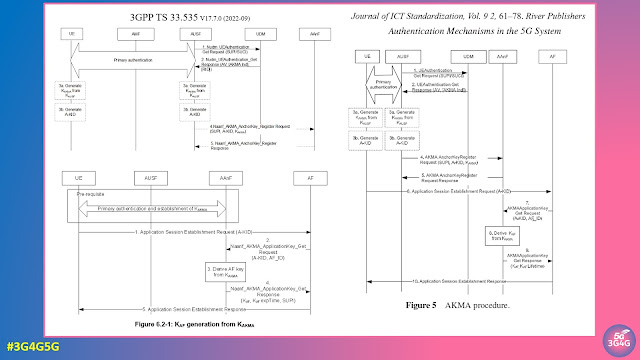
- The 3G4G Blog: Authentication and Key Management for Applications (AKMA) based on 3GPP credentials in the 5G System (5GS)
- The 3G4G Blog: 5G and Cyber Security
- The 3G4G Blog: Everything you need to know about 5G Security
- 3G4G: Security in 2G, 3G, 4G & 5G Mobile Networks