The annual ETSI Security Conference returned to the French Riviera from 6 to 9 October, once again bringing together the global cybersecurity community in the beautiful surroundings of ETSI headquarters. Over 250 participants from industry, government agencies, academia, global standards bodies, and open-source communities attended, making it one of the most engaging editions to date. The four-day event featured keynotes, panel discussions, technical sessions, poster presentations and live demonstrations, offering a holistic view of today’s security challenges and tomorrow’s opportunities.
The opening day provided a broad overview of the global cybersecurity landscape, setting the tone for the week ahead. Discussions highlighted emerging trends such as the growing influence of artificial intelligence and the rapid evolution of regulatory frameworks, including the European Commission’s Cyber Resilience Act. The sessions underscored the importance of collaboration between policymakers, researchers, and standards organisations. The afternoon focused on the cyber skills gap, a recurring theme across many sectors, stressing the need for education and training to build a security-aware workforce capable of safeguarding future digital systems. Standards were identified as key enablers in bridging policy and implementation, helping to transform regulatory intent into operational resilience.
The second day examined the paradox between AI as both a risk and a defence mechanism in cybersecurity. Experts discussed how AI-driven systems can expose new vulnerabilities if developed without strong security foundations, while also offering powerful tools for detection and response. Another session addressed fraud reduction and the convergence of security strategies to protect both networks and end users. A major highlight was the discussion on the global uptake of ETSI’s consumer IoT security standard, ETSI EN 303 645. Representatives from Germany, the UK, Singapore and Japan shared national experiences implementing consumer labelling schemes based on this standard, confirming its status as a globally recognised baseline for IoT security.
3GPP SA3 Update from ETSI Security Conference 2025 - https://t.co/COyRhvGcfQ#Free5Gtraining #3G4G5G #3GPP #5G #5GAdvanced #6G #ETSI #TheStandardsPeople #SecurityConference #3GPPSA3 #Release19 #Release20 #Release21 pic.twitter.com/dYWlNm1xWf
— Free 5G Training (@5Gtraining) October 13, 2025
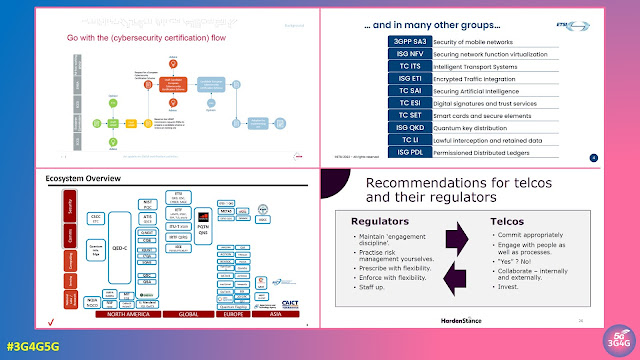
The third day was dedicated to the evolution of communication technologies and the emerging security landscape as the world moves towards 6G. Chaired by Dario Sabella from xFlow Research, the morning session explored how the journey from 5G Advanced to 6G requires a fresh approach to network security. The day began with an update from Alain Sultan of ETSI on the ongoing work within 3GPP SA3, focusing on strengthening frameworks for new architectures and deployment models. Bengt Salin from Ericsson outlined what should be considered in shaping security for 6G, emphasising that the next generation must be secure by design, not by adaptation. Nauman Khan from STC analysed the threat landscape surrounding 5G MEC and private networks, noting that as edge computing becomes more widespread, it introduces new vulnerabilities but also provides insights that can guide 6G security frameworks. Leyi Zhang from ZTE then presented on Secure Space-Air-Ground Integrated Networks, a concept uniting terrestrial, aerial, and satellite systems to provide ubiquitous connectivity. Ensuring trust, authentication, and data protection across such a heterogeneous environment presents one of the greatest challenges for 6G.
A panel discussion moderated by Dario Sabella brought together the morning’s speakers to reflect on security priorities toward 6G. The consensus was clear: while 6G is still in the early stages of standardisation, security must not be an afterthought. Lessons from 5G—particularly regarding openness, complexity, and trust—must inform the architecture and design principles of 6G from the outset. The afternoon sessions continued with broader discussions about digital sovereignty, fragmentation, and whether the internet is moving toward a “splinternet”. The day concluded with a deep dive into post-quantum cryptography, where real-world implementations provided valuable lessons for securing the next era of communication systems.
The final day of the conference shifted attention to geopolitics, cyber resilience, and the role of standards in shaping strategic responses to global challenges. Speakers explored how critical infrastructure security is increasingly influenced by geopolitical dynamics and how coordinated international standards can help mitigate risks. The Cyber Resilience Act remained a focal point, with experts emphasising the urgency of developing the 19 associated ETSI standards to support implementation. Harmonising global labelling schemes based on ETSI EN 303 645 was identified as an immediate priority, while in the longer term, education—both for future generations and C-level executives—was seen as essential to strengthen awareness of how standards underpin sovereignty, innovation, and competitiveness.
The 2025 edition of the ETSI Security Conference reaffirmed ETSI’s position as a central hub for cybersecurity dialogue and collaboration. From 5G and IoT to post-quantum cryptography and 6G, it showcased how security is now integral to every layer of the digital ecosystem. As the journey toward IMT-2030 continues, the message from Sophia Antipolis was clear: proactive, standards-based collaboration is the foundation of a secure connected future.
You can see the detailed agenda here. The presentations from the conference are all available here.
Related Posts: